Cyber Security Full Course | Cyber Security Training | Cyber Security Tutorial| Cybersecurity Guide
Welcome to our easytounderstand cybersecurity full course, packed with 5 hours of mustknow information! In this video, we'll break down cybersecurity into bitesized pieces, making it accessible to everyone.
Understanding Cybersecurity: What exactly is cybersecurity? Why is it so crucial in today's digital landscape? Where is it applied? We answer these fundamental questions and more.
Key Concepts: Explore essential cybersecurity terms such as confidentiality, integrity, availability, authenticity, nonrepudiation, least privilege, threats, risks, vulnerabilities, attack surface, attack vector, risk assessment, mitigations, and security controls.
Attack Strategies: Gain insight into how attacks work and why hackers employ them. We'll discuss frameworks like the MITRE ATT&CK Framework and Cyber Kill Chain, providing a structured approach to understanding and countering cyber threats.
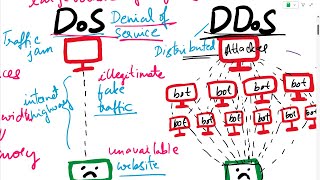
Types of Attacks: From password attacks to DoS/DDoS (DenialofService / Distributed Denial of Service) attacks, zeroday exploits, malware infections, APTs (Advanced Persistent Threats), supply chain attacks, injection attacks, crosssite scripting, social engineering, phishing, and maninthemiddle attacks, we cover a broad spectrum of attack vectors and strategies.
Security Tools: Familiarize yourself with essential security tools including EDR (Endpoint Detection and Response), antimalware software, IDS/IPS (Intrusion Detection and Prevention Systems), SIEM (Security Information and Event Management), and more.
Security Concepts: Dive into critical concepts such as incident response, security operations centers (SOCs), sandboxing, honeypots, honeynets, threat intelligence, security testing, secure SDLC (Software Development Life Cycle), defenseindepth strategies, and identity and access management.
Identity & Access Management: Explore the principles of identification, authentication, authorization, accounting, and auditing, crucial components in securing digital assets.
Secure Technologies: Learn about cryptography, including symmetric and asymmetric cryptography, digital certificates, digital signatures, virtualization, cloud computing, and the shared responsibility model in the cloud.
Cyber Security Interview Questions and Answers Playlist: • CyberSecurity Interview Questions and...
Risk Assessment in detail: • Risk Management in Cybersecurity Inf...
Different types of Malware in detail: • What is Malware | Malware Types, Risk...
Threat Modeling in detail: • Threat Modeling Explained| How to imp...
Password Attacks in detail: • Password Attacks and their Countermea...
Subscribe here: / @cyberplatter8980
CyberPlatter Discord Channel: / discord