Digital signatures using RSA - Quick Overview - Information Security- with example
Unlock the secrets of computing digital signatures using RSA with our interactive quiz guide!
Test your knowledge and master the essentials of RSA encryption in information security. Perfect for students and professionals alike.
RSA Algorithm
Key Generation:
Select two large prime numbers and
Compute =×
Compute the totient ()=(−1)×(−1)
Choose an integer
Compute such that ≡^−1 mod ()
The public key is (,) and the private key is (,).
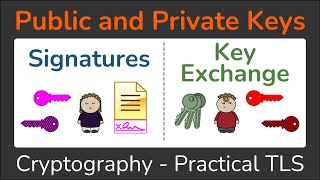
Signing the Message (sender):
Let be the message to be signed.
Compute the signature by encrypting the hash with the private key:
=()^ mod
Verifying the Signature (receiver):
To verify the signature, decrypt the signature using the public key:
M′=^ mod
If M′ matches , the signature is valid.
#InformationSecurity #RSADigitalSignature #CyberSecurity #QuizGuide #Encryption #DigitalSignatures #TechTutorial #SecureCommunications #TechEducation #CyberAwareness #LearningWithFun #Crypto #TechExplained #SecureYourData