#Hacktivity2022''navigationEndpoint':{'clickTrackingParams':'CNUBENbKAxgHIhMIpPOqp8uRiAMV4OE_BB2IugNr''commandMetadata':{'webCommandMetadata':{'url':'/hashtag/hacktivity2022''webPageType':'WEB_PAGE_TYPE_BROWSE''rootVe':6827'apiUrl':'/youtubei/v1/browse
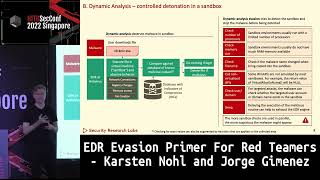
AV/EDR bypass is always a pain point but a must have of Red Team operations.
In this presentation we’ll try to understand how modern EDRs try to detect malicious activities, what are their common methodologies, and we’ll see how Red Teams (and Threat Actors) could bypass these.
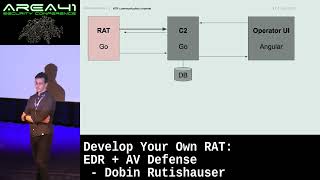
I’ll show a couple of practical techniques working against current EDR softwares, and present how these techniques could be integrated into Red Teams’ favorite C2 framework (Cobalt Strike) for making operators’ life easier.
I’ll also present an attack chain from initial compromise (partly stolen from ongoing attacks in the wild) using a stealthy staging technique, this time with the new hotness: the open source C2 Sliver.
https://www.hacktivity.com