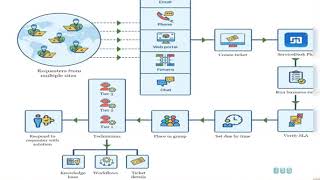
Microsoft Defender for Endpoint | RBAC | SOC Tiering | Portal Configuration
#Microsoft #Security #EndpointSecurity #MDATP #WDATP #MicrosoftDefender #MicrosoftSecurity
What is Microsoft Defender for Endpoints?
Role Based Access control in Microsoft Defender for Endpoint?
Azure AD roles which have access to Microsoft Defender for endpoint portal
Role based Access control for Microsoft Defender for Endpoint portal
SOC tiering model
Device Group
Creation of Groups In Azure AD
Creation of Roles in Microsoft Defender for Endpoint portal
Creation of Device Group in Microsoft Defender for Endpoint Portal
Assigning users to the respective roles
Microsoft Article
https://docs.microsoft.com/enus/micr...
https://docs.microsoft.com/enus/micr...
https://docs.microsoft.com/enus/micr...
Microsoft Defender What is Microsoft Defender for Endpoint? • Microsoft Defender What is Microsof...
Microsoft Defender for Endpoint Tutorial • Microsoft Defender for Endpoint Tutorial
Microsoft Defender for Endpoint Role based Access Control | SOC Tiering • Microsoft Defender for Endpoint Rol...
Microsoft Defender for Endpoint | RBAC | SOC Tiering | Portal Configuration • Microsoft Defender for Endpoint | RBA...
Onboard Windows 10 Devices | Microsoft Defender for Endpoints | MDATP | Local Script • Onboard Windows Devices | Microsoft D...
Onboard Windows Devices | Microsoft Defender for Endpoints | MDATP | Local Script • Onboard Windows Devices | Microsoft D...
Onboard Windows Devices from GPO | Microsoft Defender for Endpoint • Onboard Windows Devices from GPO | Mi...
Onboard Windows Devices from MDM | Microsoft Defender for Endpoint • Onboard Windows Devices from MDM | Mi...
Microsoft Defender for Endpoint | Onboarding Windows Server 2019 • Microsoft Defender for Endpoint | Onb...
Microsoft Defender for Endpoint | Onboarding Windows Server 2016 • Microsoft Defender for Endpoint | Onb...
Microsoft Defender for Endpoint | Onboarding Windows Server 2012 R2 • Microsoft Defender for Endpoint | Onb...
Microsoft Defender for Endpoint for Linux • Microsoft Defender for Endpoint for L...
Microsoft Defender for Endpoint | Onboarding Linux Servers • Microsoft Defender for Endpoint | Onb...
Detailed Deployment Video | Microsoft Defender For Endpoint • Detailed Deployment Video | Microsoft...
Microsoft Defender for Endpoint | Threat and Vulnerability Management • Microsoft Defender for Endpoint | Thr...
Getting Started with Threat and Vulnerability Management | Microsoft defender for Endpoint • Getting Started with Threat and Vulne...
Threat and Vulnerability Management Dashboard | Microsoft Defender for Endpoint • Threat and Vulnerability Management ...
Threat and Vulnerability Management Weaknesses | Microsoft Defender for Endpoint • Threat and Vulnerability Management ...
Security Recommendation and Remediation | Microsoft Defender for Endpoint • Security Recommendation and Remediati...
Threat and Vulnerability Management Software Inventory | Microsoft Defender for Endpoint • Threat and Vulnerability Management ...
Microsoft Defender for Endpoint | API | Basics and Fundamentals • Microsoft Defender for Endpoint | API...
Use postman to access Microsoft Defender for endpoint API • Use postman to access Microsoft Defen...
Microsoft Defender for Endpoint API | Query Any Entity Set • Microsoft Defender for Endpoint API |...
Microsoft Defender Application guard | Attack Surface Reduction • Microsoft Defender Application guard ...
Microsoft Defender Application Guard | Standalone Mode • Microsoft Defender Application Guard ...
Microsoft Defender Application Guard | Enterprise Mode | Capability Showcase • Microsoft Defender Application Guard ...
Microsoft Defender Application Guard | Enterprise Mode | Configuring GPO | Part 1 • Microsoft Defender Application Guard ...
Microsoft Defender Application Guard | Domain Joined Machine • Microsoft Defender Application Guard ...
What is attack surface reduction rule? | Microsoft Defender for Endpoint • What is attack surface reduction rule...
Attack Surface Reduction Rules | Deployment Methods and Modes • Attack Surface Reduction Rules | Depl...
Attack Surface Reduction | Deployment workflow | Microsoft Defender for Endpoint • Attack Surface Reduction | Deployment...
Configure Attack Surface Reduction rules | PowerShell • Configure Attack Surface Reduction ru...
Configure Attack Surface Reduction Rules | Group Policy • Configure Attack Surface Reduction Ru...
Deploy Attack Surface Reduction Rules from Microsoft Intune • Deploy Attack Surface Reduction Rules...
Ransomware Protection | Controlled Folder Access | Microsoft Defender for Endpoint • Ransomware Protection | Controlled Fo...
Ransomware Protection | Configure Controlled folder Access | Microsoft defender for Endpoint • Ransomware Protection | Configure Con...
Ransomware Protection | Enable Controlled Folder Access from Group Policy Object |Microsoft Defender • Ransomware Protection | Enable Contro...
Ransomware Protection | Enable Controlled Folder Access from Microsoft Intune | Microsoft Defender • Ransomware Protection | Enable Contro...