Get free YouTube views, likes and subscribers
WannaCry 2.0 - Three ways to find the Kill Switch
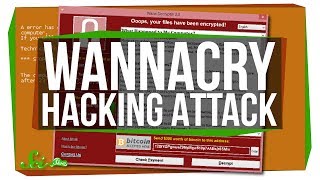
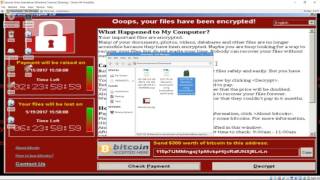
Here I demonstrate three ways you can find the Kill Switch that is hardcoded into the WannaCry 2.0 Ransomware sample. Firstly we look at the network strings in the binary using pestr. Second we run the binary and monitor the network activity in Wireshark. Third, we disassemble the binary in IDAPro and debug in Ollydgb. Sample discussed MD5: db349b97c37d22f5ea1d1841e3c89eb4
The Kill Switch domain in this sample is: hxxp://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Congrats to @MalwareTechBlog for finding this, definitely worth a follow on Twitter if you don't already.
For more Malware chat, follow me on Twitter also, / cybercdh or check out my website https://colin.guru
Recommended